Blogs
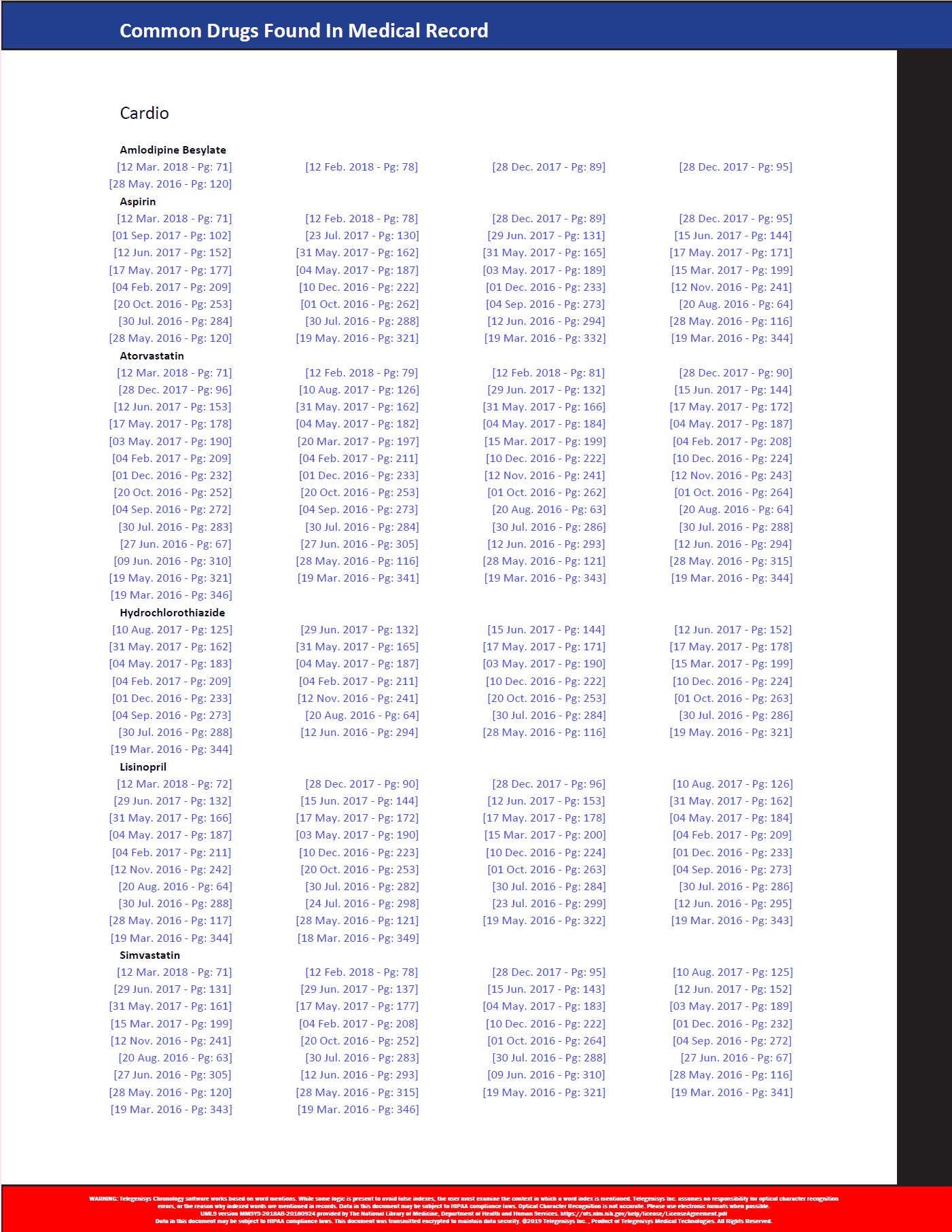
Medical chronology dense drug index support
Dense drug indexes Telegenisys often generates chronologies for medical records of over 10,000 pages. To enable our users to see drug indexes in an easy to understand and cohesive fashion our visualization team created categorized drug groupings to speed up access to...
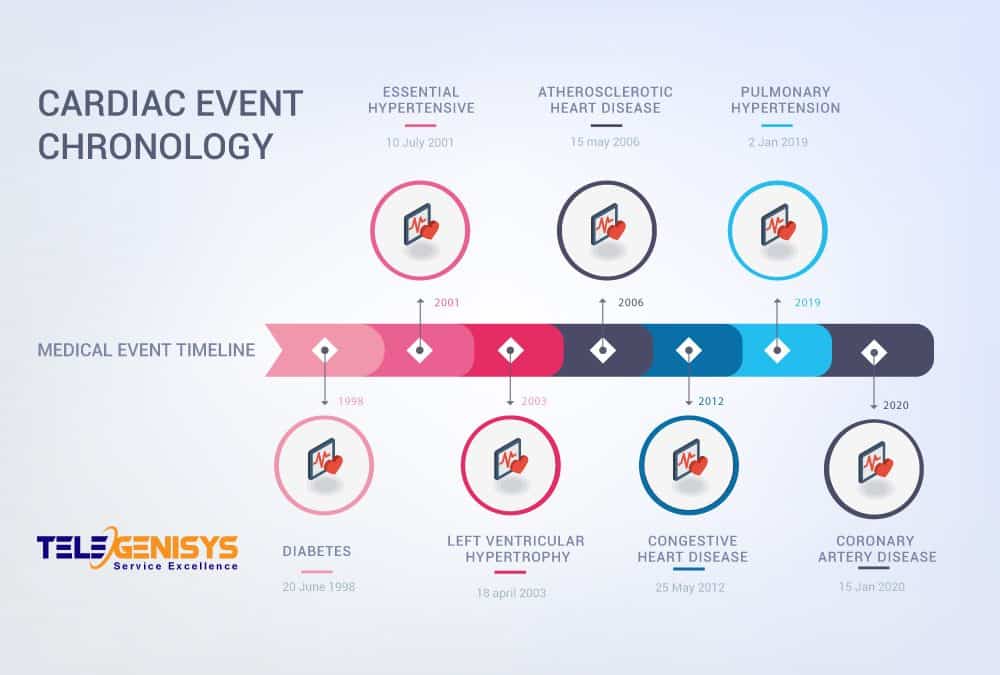
Medical chronology annual grouping display support
As Telegenisys handles more large records users requested annual groupings of chronological data. The new version of the Telegenisys Medical Chronology Software expands the data model to display both bookmarks and indexes in annual groupings making it easy to rapidly...

How are medical summaries useful to lawyers?
Medical summaries are vital for lawyers, providing a clear, concise overview of clients’ medical histories. They save time, reduce costs, and strengthen cases in personal injury and malpractice litigation.

Life expectancy abstracts for life certificates
Medical abstract components for life certificates Structured abstracts save time. Telegenisys applies client rules to put the most relevant information up front for instant access. For life certificates, abstracts are structured to provide underwriters ready to use...

HIPAA: When are business associates directly liable to safeguard PHI
The HHS office for civil rights (OCR) issued the last standard in 2013 to adjust the HIPAA privacy, Security, Breach notification, and Enforcement rules. Among different things, The last principle distinguishes arrangements of the HIPAA Rules that apply straight...

Medical chronologies should be medical grade
After over 2 years of research, Telegenisys has developed the most authoritative Medical record indexing and medical summary/chronology format for attorneys involved in personal injury actions. Using this format, attorneys can look at medical facts in several...
Are you protected against malware hidden in DICOM file format?
Cylera labs recently researched and published their study on a "flaw" in the DICOM image format for communication of medical imaging information could be exploited to hide malware in MRI and CT scans alongside other patient data. This weakness in the DICOM image file...

Outsourcing – A new business approach towards workforce management
"Over the past few years, a great many business leaders have adopted a new approach to their workforce by turning their back on traditional employees in favor of outsourced professionals. even the admin, call answering and customer service function is being delivered...

Are you sharing PHI with vendors without signing BAA?
Maintaining sufficient HIPAA-compliance standards within an organization is necessary, however, there are circumstances when PHI is shared with the vendors through data-storage services, communication providers, or document-disposal companies. HHS has provided...

Telegenisys’s Pune office celebrated Indian independence day on august 15th
Telegenisys's Pune office celebrated Indian independence day on Aug 15th. With an average tenure over 2.5 years, Telegenisys is a great place to work and maintains a high level of employee morale. Telegenisys works on highly sensitive private data for many clients and...