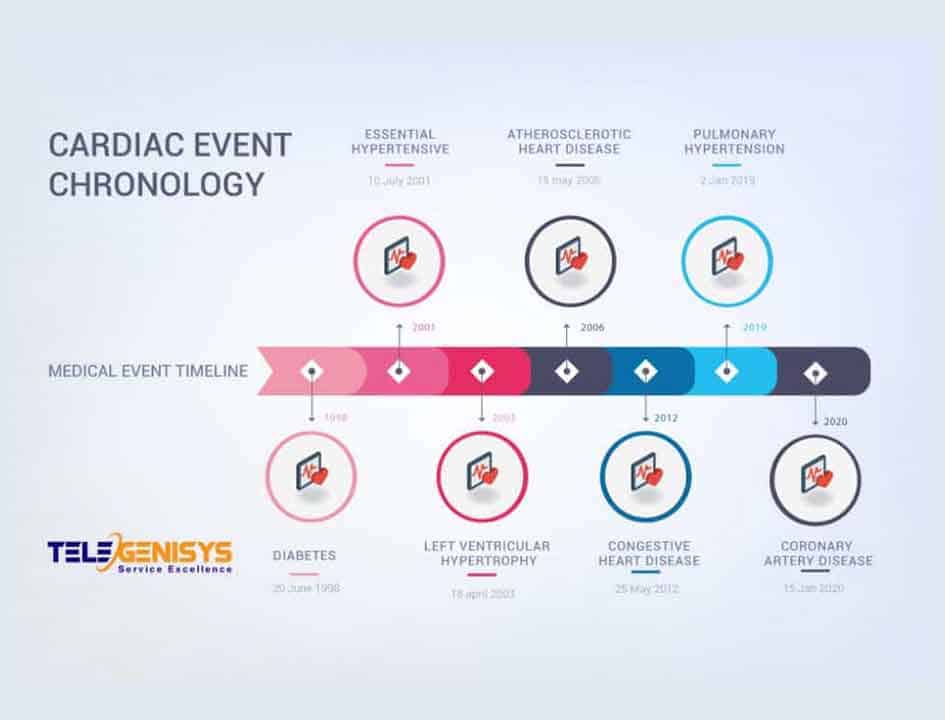
Stephen Treglia writes in the New York Law Journal that "businesses are demanding law firms sign written agreements affirming their compliance with whatever regulatory requirements are faced by the client. As part of a HIPPA, DFS, GDPR relationship, clients will...